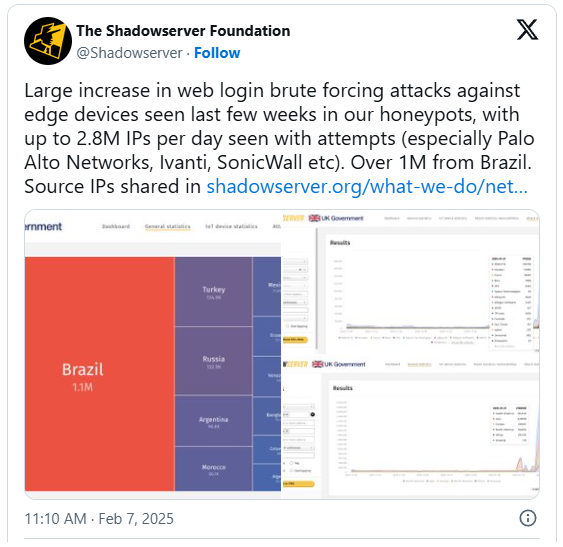
In an effort to guess the login credentials for a variety of networking devices, including those made by Palo Alto Networks, Ivanti, and SonicWall, a massive brute force password attack employing nearly 2.8 million IP addresses is now in progress.
When threat actors try to repeatedly log into a device or account using a large number of usernames and passwords until they find the right combination, this is known as a brute force attack. Once the threat actors obtain the right credentials, they can use them to access a network or take control of a device.
The Shadowserver Foundation, a threat monitoring platform, claims that a brute force attack has been going on since last month, using around 2.8 million source IP addresses every day to carry out these attacks.
Though there are typically a very large number of countries of origin taking part in the activity, the most of these (1.1 million) are from Brazil, followed by Turkey, Russia, Argentina, Morocco, and Mexico.
In order to enable remote access, these edge security devices—which include firewalls, VPNs, gateways, and other security appliances—are frequently left open to the internet. Large malware botnets frequently infiltrate MikroTik, Huawei, Cisco, Boa, and ZTE routers and Internet of Things devices, which are the primary targets of these attacks.
The Shadowserver Foundation acknowledged that although the activity has been going on for some time, it has recently grown significantly in scope. Additionally, according to ShadowServer, the assaulting IP addresses are dispersed among numerous networks and autonomous systems and are most likely a botnet or other activity connected to home proxy networks.
Residential proxies, which are IP addresses linked to Internet service provider (ISP) customers, are in high demand for usage in a variety of activities, including ad verification, scraping, cybercrime, sneaker/ticket scalping, and circumventing geo-restrictions.
By passing internet traffic over household networks, these proxies give the impression that the user is a typical home user rather than a hacker, data scraper, or bot. In residential proxying operations, gateway devices like the ones this activity targets could be used as proxy exit nodes, directing harmful data via the enterprise network of a company.
These nodes are regarded as “high-quality” since the organizations are well-known and the attacks are more difficult to identify and thwart.
Changing the default admin password to a strong and distinct one, implementing multi-factor authentication (MFA), employing an allowlist of trustworthy IPs, and turning down web admin interfaces when not in use are some ways to defend edge devices against brute-forcing assaults. In the end, patching those devices with the most recent firmware and security upgrades is essential to removing flaws that threat actors could use to obtain first access.
Changing the default admin password to a strong and distinct one, implementing multi-factor authentication (MFA), employing an allowlist of trustworthy IPs, and turning down web admin interfaces when not in use are some ways to defend edge devices against brute-forcing assaults. In the end, patching those devices with the most recent firmware and security upgrades is essential to removing flaws that threat actors could use to obtain first access.
Using a secure VPN is essential for protecting your online privacy, encrypting your internet traffic, and keeping your data safe from hackers, ISPs, and other third parties. NordVPN is one of the best and most trusted VPN providers, offering military-grade encryption, a strict no-logs policy, and advanced security features like Threat Protection and Double VPN. With thousands of servers in over 60 countries, NordVPN ensures fast and reliable connections, making it perfect for browsing, streaming, and staying anonymous online. If you’re serious about security and privacy, NordVPN is a top choice—get started today and enjoy a safer internet experience!